Scams in America and How They Are Evolving
Tis the season to be jolly but it’s also the season to be on “high alert” for anything that may look, sound or feel like a scam- this includes being extra mindful and checking your credit card statements routinely to watch for any fraudulent activity!
By now we know that there are a handful of scams out there preying on older adults whereby fraudsters pretend to be someone from the Social Security Administration, Medicare/Medicaid, a volunteer for a disaster relief charitable organization, a representative announcing that you’re a contest or sweepstake winner, or even impersonating a family member or grandchild!! However, it is important to note that scammers do not discriminate and that anyone can fall victim to their deceitful ways regardless of their age. Over the years, scammers have become skilled in making themselves look and sound legitimate but perhaps the most convincing evolution of scams are the phishing emails that these con artists are sending that are hitting inboxes across the globe!
Phishing is the fraudulent practice of sending emails alleging to be from trusted, reputable companies in order to obtain personal and sensitive information from individuals such as passwords, credit card numbers, social security numbers etc. With the latest technological advances, it can be difficult to decipher a legitimate email from a fraudulent one which is why it is critical to educate yourself on how to recognize phishing and how to protect yourself from phishing attacks.
Per the Federal Trade Commission, phishing emails often tell a story to entice you to click a link or open a corrupt attachment. All phishing emails have a call-to-action which could be any of the following:
- An “alert” comes in saying the company has “noticed some suspicious activity or log-in attempts” and they ask the receiver to click on a link to verify the “activity” on their account
- A claim is made that “there is a problem with your account or payment information” and the receiver is encouraged to click a link to update payment information
- An email comes in from what appears to be a trusted source asking for the receiver to confirm some personal information
- An invoice or similar legitimate-looking attachment is sent via email directing the receiver to open the file (which is corrupt) and then infects the receiver’s computer and/or smartphone
- A “courtesy late payment notice” is sent with a link encouraging the receiver to click to make a payment
- An email offering free services, goods or claiming eligibility for government refunds is sent promising these things to the receiver in exchange for some personal information
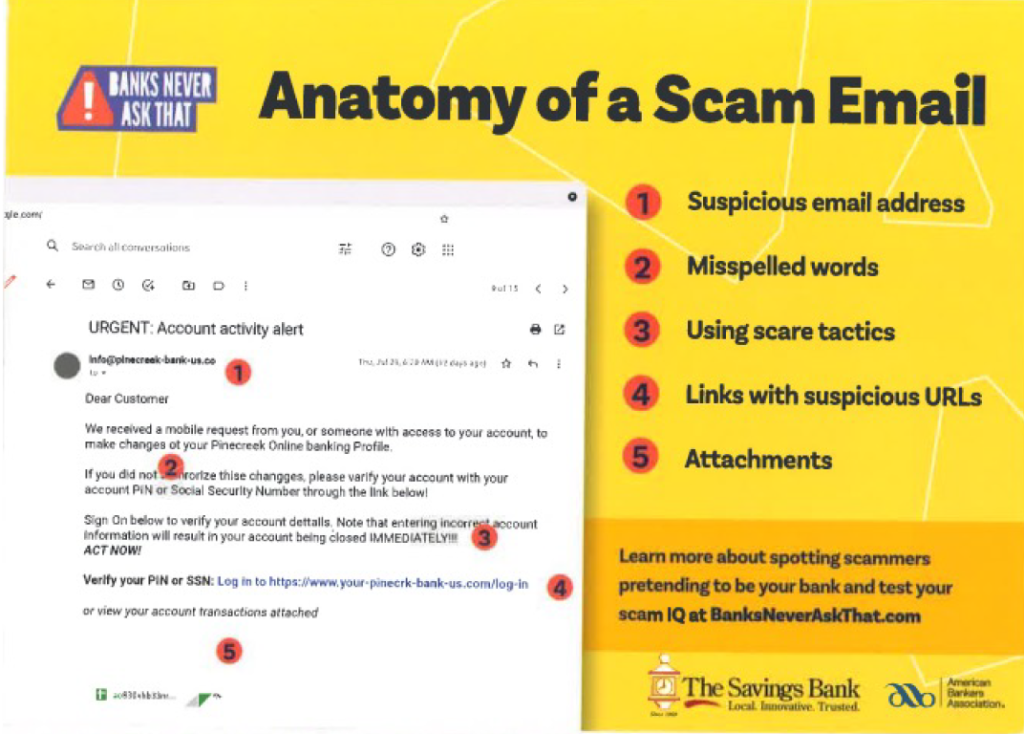
As if it wasn’t enough that fraudsters are trying to solicit credit card information and other sensitive information from individuals, they are now trying to hijack bank and routing information to gain access to victims’ accounts! The worst part about this is that scammers are successful with this given that they are so good at making their emails look like they are legitimately from the victims’ financial institutions. To protect yourself from your bank information being compromised, it is important to know what banks will ask for and what they won’t as well as what kind of emails they will send and what kind of emails they will not send. The graphic below is a helpful tool to keep handy to help you determine whether an email from your bank is fraudulent or not:
Knowledge is power and the best way to arm yourself against scamming attacks is to be vigilant when clicking on links, opening attachments and/or responding to emails. To help protect yourself from phishing, the Federal Trade Commission encourages the following:
- Protect your computer and other smart devices with security software and malware protection– setting the software to update automatically so it can handle new security threats
- Protect your accounts by using multi-factor authentication whereby you would need to provide two or more credentials to log in to your account
- Protect your data by backing it up to an external hard drive or secure cloud storage and not just relying on your home network
- NEVER give out your personal, sensitive information over email or over the phone unless you are 100% sure you can trust the source